A Deep Dive into Windows Hello (2) - Hackers In inTrusion Laboratory

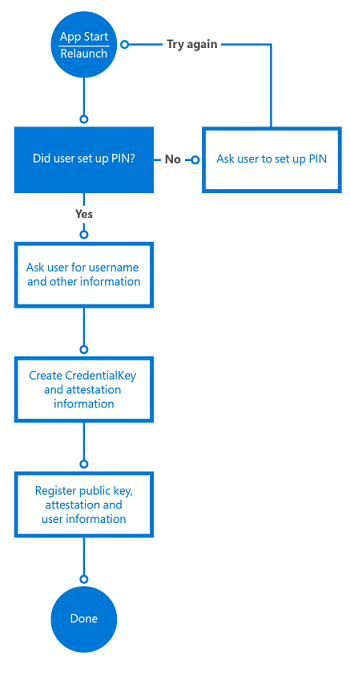
Client-side Login Procedures With protocol analysis, we figure out what data is exchanged between the client and the server for Windows Hello login. Now we’d like to know where is authentication data stored in the client-side? And how authentication data is used to? For these, we performed static and dynamic debugging for login-related services on … Continue reading A Deep Dive into Windows Hello (2) →

Cyber Security Courses Free

TuxCare Blog - Insights and News on Linux Technology

Bypassing Windows Hello Without Masks or Plastic Surgery

Bypassing Windows Hello Without Masks or Plastic Surgery

Game of Tokens: AD post exploitation with Token Impersonation, by Jinendar Kothari

Hacker techniques, exploit and incident handling
Is it possible to get a trusted hacker? - Quora

Blue Team Hacking Intrusion Detection with Snort

A Deep Dive into Windows Hello (2) - Hackers In inTrusion Laboratory

Series 02 — Encryption and Firewalls, by Sushrita Swain, Jan, 2024
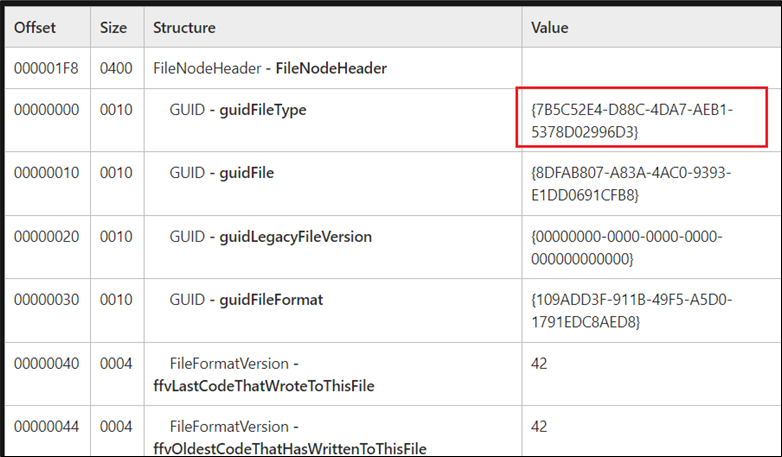
The Rising Trend of OneNote Documents for Malware delivery

Live Demo: Hack your first computer with Immersive Labs

The Art of Invisibility: The World's Most Famous Hacker Teaches You How to Be Safe in the Age of Big Brother and Big Data: Mitnick, Kevin, Vamosi, Robert, Hypponen, Mikko: 9780316380508:

Law & Innovation Lab Sturm College of Law
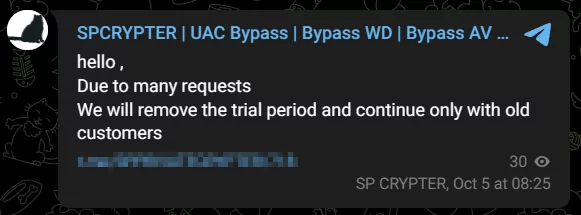
Nightmangle' Telegram C2 Agent and New FUD Crypter with Windows Defender Bypass